John the Ripper
This exercise complements material in the CompTIA Security+: Get Certified Get Ahead: SY0-701 Study Guide.
Background. One of the methods of cracking a password is using a dictionary, or file filled with words. This lab demonstrates how John the Ripper uses a dictionary to crack passwords for Linux accounts.
Prerequisites. Launch a terminal within a Linux operating system. If you’re not sure how, follow the steps in the study guide to do so.
Note: This lab assumes you are using Kali Linux Installed in the Kali Linux lab. It also assumes you are using the root account. If you are using a different distribution, some of these commands may need to be slightly modified to match that distribution.
Create an Account for Homer in Linux
Note. You will be cracking the password for this account.
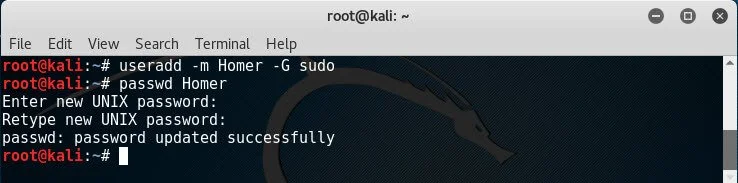
1. Use the following command to create an account named Homer. The -G switch adds the account to the super user group.
useradd -m Homer -G sudo
Note: Using a USB to boot into Linux (such as Ubuntu Linux Mint 19.1 Cinnamon https://amzn.to/2HVAFnB), instead of the Kali Linux distribution, this didn’t work. For this distribution, you can enter the following command:
sudo useradd Homer
2. Use the following command to set the password for the account you just created.
passwd Homer
Note: Using a USB to boot into Linux (such as Ubuntu Linux Mint 19.1 Cinnamon https://amzn.to/2HVAFnB), instead of the Kali Linux distribution, this didn’t work. For this distribution, you can enter the following command:
sudo passwd Homer
3. Enter a simple password for this user. Enter password twice.
Use Unshadow to Create a File with Username and Password details
Note that the two directories you are combining are:
/etc/passwd
/etc/shadow
If you’re using a Kali Linux distribution and you haven’t added any other accounts, these directories will include the root account and the account you created earlier.
1. Run the following command to combine the passwd and shadow directories and store them in a single file in the local directory.
unshadow /etc/passwd /etc/shadow > userpwds
If you are using Ubuntu Linux Mint 19.1 Cinnamon (https://amzn.to/2HVAFnB) to boot into a Linux distro from the USB drive, this command will work instead:
sudo unshadow /etc/passwd /etc/shadow > userpwds
2. Enter the following command to verify the file named userpwds was created and exists in the current directory.
ls -l
View the Password List
Kali Linux includes a password list within the /usr/share/john/ folder named password.lst. You can use these steps to view the password list within a text editor.
1. Use the following command to open the password list in the text editor Vim.
vim /usr/share/john/password.lst
Note that you can scroll through the list using the up and down arrows, and page up and page down keys.
2. To exit the Vim text editor press the colon key (:), then press q, and then press enter. This quits the text editor without changing any contents.
Crack the Passwords
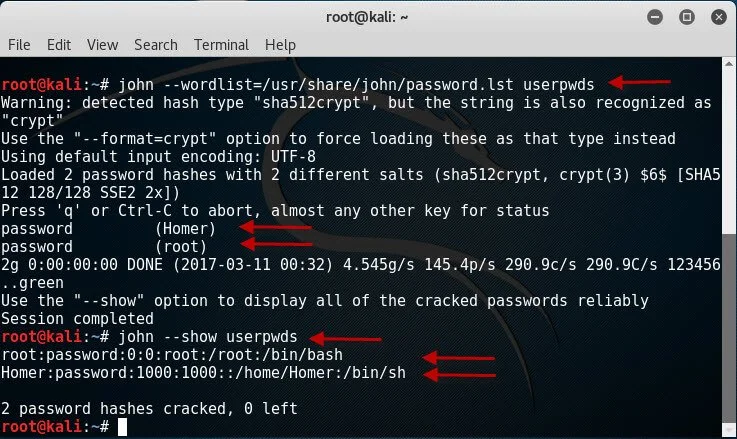
1. Use the following command to discover the passwords in the combined unshadow file.
john – -wordlist=/usr/share/john/password.lst userpwds
If you are using Ubuntu Linux Mint 19.1 Cinnamon (https://amzn.to/2HVAFnB) to boot into a Linux distro from the USB drive, this command will work instead:
sudo john -wordlist=/usr/share/john/password.lst userpwds -format=crypt
2. User the following command to show the details on the accounts including their passwords.
john – -show userpwds
If you are using Ubuntu Linux Mint 19.1 Cinnamon (https://amzn.to/2HVAFnB) to boot into a Linux distro from the USB drive, this command will work instead:
sudo john -show userpwds
Note that the figure shows that both of these accounts have simple passwords of password.
Want to do some more?
If desired, you can change Homer’s password and redo the commands. Note that with a more complex password, it might take longer to crack. Also, if you use a strong complex password that isn’t in the password list, you’ll find that John the Ripper won’t be able to crack it.
Delete the Account
If desired, you can delete the account you created for this lab with the following command: userdel Homer