Appendix C
Well-Known Ports
CompTIA has deemphasized ports in recent exams. However, they may still include them in tests. Additionally, some test-takers don’t fully understand how ports are used. This appendix may fill in some holes for you and will give you a reminder of the ports in case you need it.
Port Basics
Ports are logical numbers used by TCP/IP to identify what service or application should handle data
received by a system. Both TCP and UDP use ports with a total of 65,536 TCP ports (0 to 65,535) and
65,536 UDP ports (0 to 65,535). Administrators open ports on firewalls and routers to allow the
associated protocol into or out of a network. For example, Hypertext Transfer Protocol (HTTP) uses port 80, and an administrator allows HTTP traffic by opening port 80.
Additionally, administrators disable unnecessary ports and services as part of a basic security
practice. These ports and services are associated with specific protocols and if they are disabled, it blocks any attacks on these ports, services, and protocols.
The Internet Assigned Numbers Authority (IANA) maintains a list of official port assignments that
you can view at https://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.xhtml.
IANA divided the ports into three ranges, as follows:
Well-known ports: 0–1023. IANA assigns port numbers to commonly used protocols in the well-known ports range.
Registered ports: 1024–49,151. IANA registers these ports for companies as a convenience to the IT community. A single company may register a port for proprietary use, or multiple companies may use the same port for a specific standard. As an example, Microsoft SQL Server uses port 1433 for database servers, Layer 2 Tunneling Protocol (L2TP) uses port 1701, and Point-to-Point Tunneling Protocol (PPTP) uses port 1723.
Dynamic and private ports: 49,152–65,535. These ports are available for use by any application. Applications commonly use these ports to map an application to a port temporarily. These temporary port mappings are often called ephemeral ports, indicating that they are short-lived.
Although virtually all the ports are subject to attack, most port attacks are against the well-known ports. Port scanners often simply check to see if a well-known port is open. For example, SMTP uses the well-known port 25, so if port 25 is open, the system is likely running SMTP.
Network administrators who regularly work with routers and firewalls can easily tell you which protocol is associated with which well-known port, such as 20, 21, 22, 23, 25, 80, 443, and so on. The reason is that they use these ports to allow or block traffic.
For example, an administrator can close port 25 to block all SMTP traffic into a network. The router then ignores traffic on port 25 instead of forwarding it. Similarly, an administrator can close port 1433 to block database traffic to a Microsoft SQL server. On the other hand, the administrator can open port 25 or port 1433 to allow SMTP traffic or traffic to a Microsoft SQL server, respectfully.
Although ports are second nature to router and firewall administrators, they might not be so familiar to you. If you don’t work with the ports often, you’ll need to spend some extra time studying to ensure you’re ready for the exam.
Combining the IP Address and the Port
At any moment, a computer could be receiving dozens of packets, and each of these packets includes a destination IP address and a destination port. TCP/IP uses the IP address to get the packet to the computer. The computer then uses the port number to get the packet to the correct service, protocol, or application that can process it.
For example, if the packet has a destination port of 443, the well-known port for Hypertext Transfer Protocol Secure (HTTPS), the system passes the packet to the process handling HTTPS. It wouldn’t do much good to pass an SMTP email packet to the HTTPS service or send an HTTPS request packet to the SMTP service.
IP Address Used to Locate Hosts
Imagine that the IP address of GetCertifiedGetAhead.com is 35.221.53.172, and the address assigned to your computer in an internal network is 192.168.10.11. TCP/IP uses these IP addresses to get the packets from your computer to the web server and the web server’s answer back to your computer.
There’s a lot more that occurs under the hood with TCP/IP (such as DNS, NAT, and ARP), but the main point is that the server’s IP address is used to get the requesting packet from your computer to the server. The server gets the response packets back to your computer using your IP address (or the IP address of your NAT server).
SErver Ports
Different protocols are enabled and running on a server. These protocols have well-known or registered port numbers, such as port 22 for SSH, 25 for SMTP, 80 for HTTP, 443 for HTTPS, and so on. When the system receives traffic with a destination of port 443, the system knows to send it to the service handling HTTPS.
Any web browser knows that the well-known port for HTTPS is 443. Even though you don’t see port 443 in the URL, it is implied as HTTPS://GetCertifiedGetAhead.com:443. If you omit the port number, HTTPS uses the well-known port number 443 by default.
Popular web servers on the Internet include Apache and Internet Information Services (IIS). Apache is free and runs on Unix or Linux systems. Apache can also run on other platforms, such as Microsoft systems. IIS is included in Microsoft Server products. These web servers use port 443 for HTTPS. When the server receives a packet with a destination port of 443, the server sends the packet to the web server application (Apache or IIS) that processes it and sends back a response.
Client Ports
TCP/IP works with the client operating system to maintain a table of client-side ports using available ports in the dynamic and private ports range. This table associates port numbers with different applications that are expecting return traffic. Client-side ports start at port 49,152 and increment up to 65,535. If the system uses all the ports between 49,152 and 65,535 before being rebooted, it’ll start over at 49,152.
When you use your web browser to request a page from a site, your system will record an unused client port number such as 49,152 in an internal table to handle the return traffic. When the web server returns the webpage, it includes the client port as a destination port. When the client receives webpage packets with a destination port of 49,152, it sends these packets to the web browser application. The browser processes the packets and displays the page.
Putting It All Together
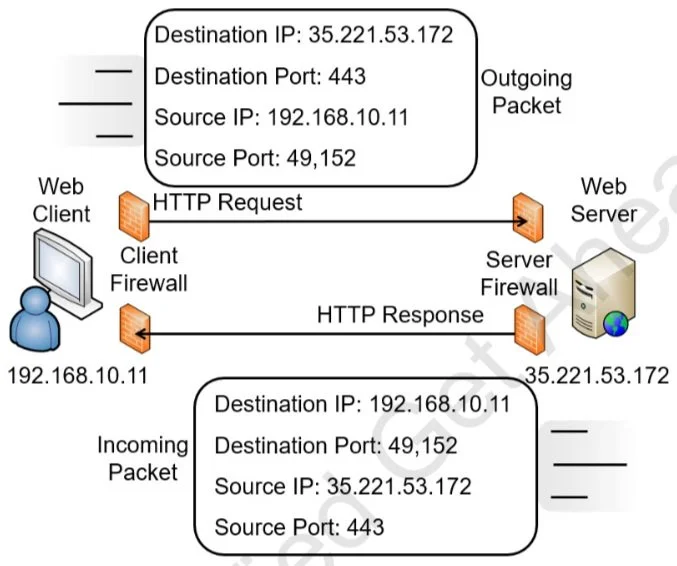
The previous section described the different pieces, but it’s useful to put this together into a single description. Imagine that you decide to visit the website https://GetCertifiedGetAhead.com using your web browser, so you type the URL into the browser, and the webpage appears. Here are the details of what is happening. Figure C.1 provides an overview of how this will look, and the following text explains the process.
Figure C.1: Using source and destination ports
Your computer creates a packet with source and destination IP addresses and source and destination ports. It queries a DNS server for the IP address of GetCertifiedGetAhead.com and learns that the IP address is 35.221.53.172. Additionally, your computer will use its IP address as the source IP address. For this example, imagine your computer’s IP address is 192.168.10.11.
Because the web server is serving webpages using HTTPS and the well-known port is used, thedestination port is 443. Your computer will identify an unused port in the dynamic and private ports range (a port number between 49,152 and 65,535) and map that port to the web browser. For this example, imagine it assigns 49,152 to the web browser. It uses this as the source port.
At this point, the outgoing packet has both destination and source data as follows:
Destination IP address: 35.221.53.172 (the web server)
Destination port: 443
Source IP address: 192.168.10.11 (your computer)
Source port: 49,152
TCP/IP uses the IP address (35.221.53.172) to get the packet to the GetCertifiedGetAhead web server. When it reaches the web server, the server looks at the destination port (443) and determines that the packet needs to go to the web server program servicing HTTPS. The web server creates the page and puts the data into one or more return packets. At this point, the source and destinations are swapped because the packet is coming from the server back to you:
Destination IP address: 192.168.10.11 (your computer)
Destination port: 49,152
Source IP address: 35.221.53.172 (the web server)
Source port: 443
Again, TCP/IP uses the IP address to get the packets to the destination. Once the packets reach your system, it sends them to the destination port (port 49,152). Because your system mapped this port to your web browser, it sends the packets to the web browser, displaying the webpage.
The Importance of Ports in Security
Routers, and the routing component of firewalls, filter packets based on IP addresses, ports, and some protocols such as ICMP or IPsec. Because many protocols use well-known ports, you can control protocol traffic by allowing or blocking traffic based on the port.
In the previous example, the client firewall must allow outgoing traffic on port 443. Firewalls automatically determine the client ports used for return traffic, and if they allow the outgoing traffic, they allow the return traffic. In other words, because the firewall allows the packet to go to the web server on the destination port of 443, it also allows the webpage to return on the dynamic source port of 49,152.
Note that the client firewall doesn’t need to allow incoming traffic on port 443 for this to work. The web client isn’t hosting a web server with HTTPS, so the client firewall would block incoming traffic on port 443. However, the firewall that is allowing traffic to the web server needs to allow incoming traffic on port 443.
You can apply this same principle to any protocol and port. For example, if you want to allow SMTP traffic, you create a rule on the firewall to allow traffic on port 25 or port 587 for SMTP encrypted with TLS. IT professionals modifying access control lists (ACLs) on routers and firewalls commonly refer to this as opening a port to allow traffic or closing a port to block traffic.
Comparing Ports and Protocol Numbers
Ports and protocol numbers are not the same things, though they are often confused. Well-known ports identify many services or protocols, as discussed previously.
However, many protocols are not identified by the port but instead by the protocol numbers. For example, within Internet Protocol security (IPsec), protocol number 50 indicates the packet is an Encapsulating Security Payload (ESP) packet, and protocol number 51 indicates it’s an Authentication Header (AH) packet. Similarly, ICMP uses the protocol number of 1, TCP is 6, and UDP is 17.
You can use a protocol number to block or allow traffic on routers and firewalls just as you can block or allow traffic based on the port. Note that it is not accurate to say that you can allow IPsec ESP traffic by opening port 50. IANA lists port 50 as a Remote Mail Checking Protocol. However, you can allow IPsec traffic by allowing traffic using protocol number 50.
Port Tables
The following tables show many of the well-known ports that you may need to know when taking the CompTIA Security+ exam
- Protocol
- Port
- Protocol
- Port
- SMPT
- TCP 25
- SMTP TLS/SSL
- TCP 587
- IMAP4
- TCP 143
- Secure IMAP4
- TCP 993
- POP3
- TCP 110
- Secure POP
- TCP 995
- SSH
- TCP 22
- TLS
- TCP 443
- FTP data port (active mode)
- TCP 21
- SFTP(uses SSH)
- TCP 22
- FTP (PASV) control
- TCP 21
- FTPS(uses TSL)
- TCP 989
- FTP control
- TCP 20
- FTPS(uses TLS)
- TCP 990
- TFTP
- UDP 69
- SCP(uses SSH)
- TCP 22
- HTTP
- TCP 80
- HTTPS (uses TLS)
- TCP 443
- DNS name queries
- UDP 53
- DNS zone transfers
- TCP 53
Table C.1: Ports and protocols
- Protocol
- Port
- Protocol
- Port
- NetBIOS (TCP rarely used)
- TCP/UDP 137
- LDAP
- TCP 389
- NetBIOS
- UDP 138
- LDAPS
- TCP 636
- NetBIOS
- TCP 139
- Telnet (not recommended)
- TCP 23
- L2TP
- UDP 1701
- IPsec (for VPN with IKE)
- UDP 500
- PPTP
- TCP 1723
- Remote Desktop Protocol (RDP)
- TCP/UDP 3389
- SNMP
- UDP 161
- SNMP trap
- UDP 162
- SIP
- TCP 5060/5061
- SMB
- TCP 445
- DHCP (client to server)
- UDP 67/68
- DHCP (server to client)
- UDP 68
- RADIUS
- UDP 1812/1823
- RADIUS with EAP
- TCP 1812
- TACACS+
- TCP 49
- Kerberos
- TCP/UDP 88
Table C.2: Ports and protocols